Export GPG Subkeys to Yubikey
Exports GPG subkeys to Yubikey so master key can remain offline while still using GPG keys. See GPG Master Key to create GPG keys and setup operating systems to use Yubikeys for GPG key material.
Understanding How Yubikeys Work
Read the technical manual to understand how Yubikeys work. This will setup
the Yubikey to use the CCID interface to setup openpgp on the key.
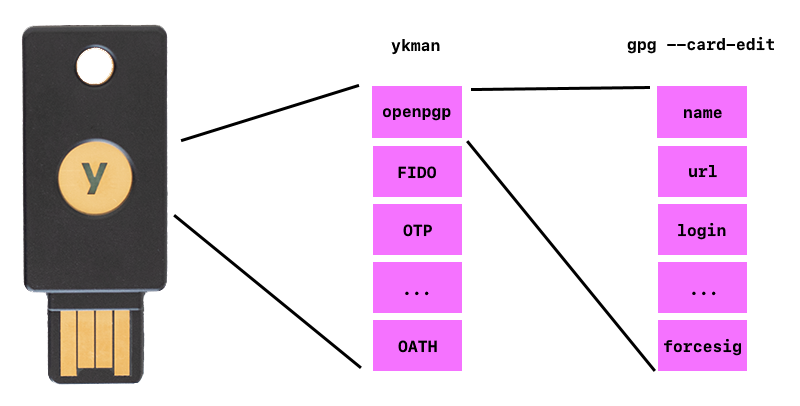
Yubikey manager is an application that is used to manage the Yubikey
itself (ykman) and sets how applets are used on the key. The configuration
of the applets themselves are managed by respective apps, in this case GPG.
Note
ykmanwill set preferences like number of applet PIN attempts, PINs, and touch preferences.gpg --edit-cardwill set openpgp configuration, like PGP name, login, url.
Export Subkeys to Yubikeys
Danger
Exporting keys to Yubikey will destroy the local key. Ensure a backup has been made before doing this (so original state can be restored). See Backup GPG Keys and Restore Original GPG State respectively.
$ gpg --edit-key $KEYID
gpg> key 1
sec rsa4096/################
created: 2019-01-01 expires: never usage: C
trust: ultimate validity: ultimate
ssb* rsa4096/################
created: 2019-01-01 expires: never usage: S
ssb rsa4096/################
created: 2019-01-01 expires: never usage: E
ssb rsa4096/################
created: 2019-01-01 expires: never usage: A
[ultimate] (1). FIRST LAST <EMAIL>
gpg> keytocard
Please select where to store the key:
(1) Signature key
(3) Authentication key
Your selection? 1
You need a passphrase to unlock the secret key for user: "FIRST LAST <EMAIL>"
4096-bit RSA key, ID ################, created 2019-01-01
gpg> save
Note
Key selection is a toggle, ensure to only export one key at a time; this is
denoted by a *.
First Password: GPG private key password.
Second Password: Yubikey user term:PIN.
$ gpg --edit-key $KEYID
gpg> key 2
sec rsa4096/################
created: 2019-01-01 expires: never usage: C
trust: ultimate validity: ultimate
ssb rsa4096/################
created: 2019-01-01 expires: never usage: S
ssb* rsa4096/################
created: 2019-01-01 expires: never usage: E
ssb rsa4096/################
created: 2019-01-01 expires: never usage: A
[ultimate] (1). FIRST LAST <EMAIL>
gpg> keytocard
Please select where to store the key:
(2) Encryption key
Your selection? 2
You need a passphrase to unlock the secret key for user: "FIRST LAST <EMAIL>"
4096-bit RSA key, ID ################, created 2019-01-01
gpg> save
Note
Key selection is a toggle, ensure to only export one key at a time; this is
denoted by a *.
First Password: GPG private key password.
Second Password: Yubikey user term:PIN.
$ gpg --edit-key $KEYID
gpg> key 3
sec rsa4096/################
created: 2019-01-01 expires: never usage: C
trust: ultimate validity: ultimate
ssb rsa4096/################
created: 2019-01-01 expires: never usage: S
ssb rsa4096/################
created: 2019-01-01 expires: never usage: E
ssb* rsa4096/################
created: 2019-01-01 expires: never usage: A
[ultimate] (1). FIRST LAST <EMAIL>
gpg> keytocard
Please select where to store the key:
(3) Authentication key
Your selection? 3
You need a passphrase to unlock the secret key for user: "FIRST LAST <EMAIL>"
4096-bit RSA key, ID ################, created 2019-01-01
gpg> save
Note
Key selection is a toggle, ensure to only export one key at a time; this is
denoted by a *.
First Password: GPG private key password.
Second Password: Yubikey user PIN.
Verify subkeys are Offloaded
Offloaded keys will have > next to the key, showing that the key is on the
card.
gpg --list-secret-keys
Restore Original GPG State
The original GPG state needs to be reloaded to export subkeys to additional Yuibkeys, or to keep a pristine copy of GPG key data on encrypted storage.
cp -avi $GPGBACKUP/* $GNUPGHOME