Windows GPG Yubikey
Configure Yubikey for SSH authentication on windows.
Required Materials
gpg4win downloaded. Verify Integrity.
Yubikey manager installed. Only required if you are changing keypress and NFC settings.
Putty installed.
Pre-configured Yubikey using Export GPG Subkeys to Yubikey.
Configure GPG4win
This will provide GPG interactions as well as an agent to provide key material to putty, winscp, etc.
The system path is modified using the system preferences control panel plugin to enable gpg use anywhere on the system.
Download gpg4win
and verify integrity.
Add gpg to user system path
⌘ › sysdm.cpl › Advanced › Environment Variables › User variables for {USER} › Path › Edit › New
Path
c:\Program Files (x86)\GnuPG\bin
GPG path should be added to end of list.
Updated: 2021-02-19
Configure GPG Agent
This will enable SSH and Putty usage with the gpg-agent.
%appdata%\gnupg\scdaemon.conf reader-port Yubico YubiKey OTP+FIDO+CCID 0
Note
Yubico YubiKey OTP+FIDO+CCID 0is the device name as listed in DeviceManager. This prevents Windows Hello from attempting to act as an pagent device (resulting in no key found errors).
start › Device Manager › View › Show Hidden Devices start › Device Manager › Software Devices
The name to use will be the full Yubikey device name.
%appdata%\gnupg\gpg-agent.confenable-ssh-support
enable-putty-support
gpgconf --kill gpg-agent
"c:\Program Files (x86)\GnuPG\bin\gpg-connect-agent.exe" /bye
Configure Putty
Configure a host in putty and ensure the following options are set:
Use pageant for Putty Auth
Putty › Connection › SSH › Auth
☑
Attempt authentication using Pageant
›
Private key file for authentication
Updated: None
Be sure to save your configuration changes.
Verify Putty Works
Ensure Yubikey is readable by GPG. This assumes you already setup:
~/.ssh/authorized_keyson the target machine with your exported GPG SSH RSA Public Key; see Export GPG Keys. Reference SSH for remote SSH configuration.Trusted the GPG Master Public Key on the local machine; see Import GPG Master Public Key.
Connect with putty as normal.
A
Pin Entrypop-up window should appear. It may not be in focus. Enter your user PIN and press OK.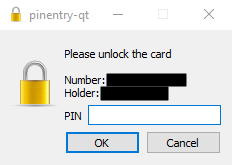
There will be no prompt in putty, but the Yubikey will start blinking. Tap Your Key to login.
Note
Number is the Yubikey serial number.
Holder is the First/Last name of the GPG certificate on the key.
Your key will blink when waiting for password or touch.
Both publickey and GPG can be used in the same system at the same time for different connections. No specific configuration is needed.
Run GPG Agent on Login
Scheduled Tasks are inconsistently applied and therefore you will run into issues if you depend on the scheduled tasks to always run at login to refresh your GPG agent. This is compounded by GPG agent occasionally hanging and needing to be force restarted. This is remedied by triggering GPG agent refresh on screen unlock events, ensuring that the agent is always ready.
See full instructions here: Scheduled Tasks Inconsistencies; or just follow these.
Forward GPG Agent Through Multiple Servers
This is effectively using a single server as an SSH Bastion and SSH’ing to additional machines through the bastion. This keeps your private credentials on your local machine, however, while the connection is active it is possible for other to use them as you while you are connected; so a secured and monitored system should be used. Machines are referred to as putty for your client machine, bastion for the machine you will be SSH’ing through and target for remote SSH targets.
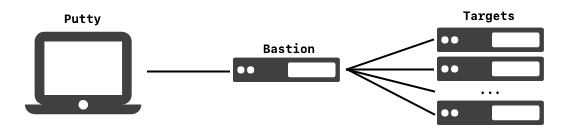
Enable GPG Agent Forwarding in Putty
Putty › Connection › SSH › Auth
☑
Allow agent forwarding
Updated: None
/etc/ssh/sshd_config on Bastion.StreamLocalBindUnlink yes
AllowAgentForwarding yes
Note
The exported GPG SSH RSA public key should be added to
~/.ssh/authorized_keysfile for the connecting user. See: Export GPG Keys.This will allow you to forward your credentials again to the next server.
Removes current socket file for forwarding before creating a new one.
sshd -T | grep -i allowagent
/etc/ssh/sshd_config on Target.AllowAgentForwarding no
Note
Target does not need to enable outbound agent forwarding for this to work.
The exported GPG SSH RSA public key should be added to
~/.ssh/authorized_keysfile for the connecting user. See: Export GPG Keys.
References