Ubuntu GPG Yubikey¶
Configure Yubikey for SSH authentication on Ubuntu.
Gnome-keyring implements both ssh-agent and gpg-agent with a broken
implementation that does not support smart cards. This will be disabled.
Required Materials¶
Pre-configured Yubikey using Export GPG Subkeys to Yubikey.
apt update && apt upgrade
apt-add-repository ppa:yubico/stable
apt update
apt install software-properties-common yubikey-manager yubikey-manager-qt scdaemon gpg pcscd
apt remove libpam-gnome-keyring
Note
yubikey-manager-qt is a GUI frontend which has limited functionality but does provide easy ways to ensure specific applets are enabled. scdaemon enables smartcard support for gpg.
Hint
Ubuntu 18.04+ needs to add universe multiverse repositories to all apt
sources in /etc/apt/sources.list.
Configure GPG Agent¶
This will enable SSH usage with the gpg-agent.
~/.gnupg/gpg-agent.conf¶enable-ssh-support
~/.gpg-yubikey¶if [ ! -f "${HOME}/.gpg-agent-info" ] && [ -S "${HOME}/.gnupg/S.gpg-agent" ] && [ -S "${HOME}/.gnupg/S.gpg-agent.ssh" ]; then
echo "GPG_AGENT_INFO=${HOME}/.gnupg/S.gpg-agent" >> "${HOME}/.gpg-agent-info";
echo "SSH_AUTH_SOCK=${HOME}/.gnupg/S.gpg-agent.ssh" >> "${HOME}/.gpg-agent-info";
fi
if [ -f "${HOME}/.gpg-agent-info" ]; then
. "${HOME}/.gpg-agent-info"
export GPG_AGENT_INFO
export SSH_AUTH_SOCK
export GPG_TTY=$(tty)
gpg-connect-agent updatestartuptty /bye >& /dev/null
fi
Download .gpg-yubikey
Setup the GPG environment when logging in with user.
~/.bash_profile¶. ~/.gpg-yubikey
~/.bashrc¶. ~/.gpg-yubikey
Allow User to Automount Yubikeys¶
/etc/udev/rules.d/99-yubikeys.rules¶ACTION=="add",SUBSYSTEM=="usb", ATTR{idVendor}=="1050", ATTR{idProduct}=="0404", OWNER="{USER}"
Note
Be sure to set OWNER to your username.
Disable Gnome SSH Fuckery¶
Disable gnome SSH agent on startup
Note
May be listed as SSH agent
Ubuntu › Settings › Session › Startup › Advanced
☐
Launch gnome services on startup
Updated: None
/etc/X11/Xsession.options¶#use-ssh-agent
Reboot.
Verify SSH Works¶
Ensure Yubikey is readable by GPG. This assumes you already setup:
~/.ssh/authorized_keyson the target machine with your exported GPG SSH RSA Public Key; see Export GPG Keys. Reference SSH for remote SSH configuration.Trusted the GPG Master Public Key on the local machine; see Import GPG Master Public Key.
Connect with SSH as normal.
A
Pin Entrypop-up window should appear. It may not be in focus. Enter your user PIN.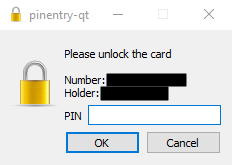
OK
There will be no prompt in putty, but the Yubikey will start blinking. Tap Your Key to login.
Note
Number is the Yubikey serial number.
Holder is the First/Last name of the GPG certificate on the key.
Your key will blink when waiting for password or touch.
References