Prep Yubikey
Attention
Yubikey Password/PINs may be up to 127 ASCII characters long.
Default Yubikey Passwords
Default User Pin |
123456 |
Default Admin Pin |
12345678 |
Verify Geniue Yubikey
Ensure Yubikey is geniue and has not been tampered with during any step of the supply chain.
Verify Device
Touch Yubikey when prompted.
Note
Yubico must be able to see the make and model of the device during the verification process.
Verification Complete is displayed for genuine keys. Failure means potential
compromise and should be thrown out after it is confirmed to fail again.
Reset Yubikey
This will destroy any openpgp material on the key and reset to the default key state. Do this even if the Yubikey is new.
ykman openpgp reset
Alternatively using the Yubikey Personalization Tool will provide options to do this via a GUI.
Note
If the Yubikey is not brand new, ensure you are not deleting any other 2FA configurations.
gpg --card-status
If not found, re-insert the key. There is a known race condition that may occur with older GPG libraries.
Ensure latest firmware version using Yubikey Manager.
Ensure device has
CCIDmode enabled using Yubikey Manager. Most firmware past3.1.8will have this permenantly enabled and not listed.
Configure Yubikey
Configure behavior of Yubikey so short touches will provide GPG material, while long touches will provide Yubico OTP. This prevents accidental touches spewing keystrokes into whatever is open. NFC is also disabled to force physical touch to use key.
Yubikey Manager › Applications › OTP
Delete
Slot 1.Configure
Slot 2to useYubico OTP.
Note
Newer keys can just use the swap button.
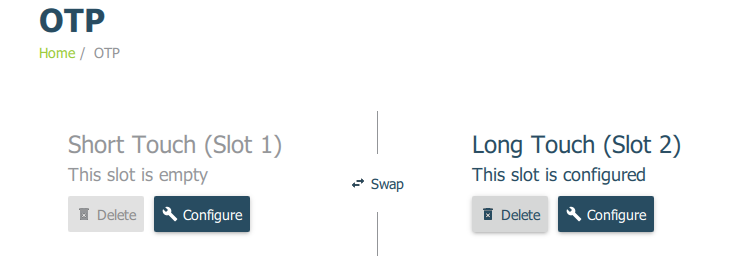
Swapped button press lengths.
Yubikey Manager › Interfaces › NFC › Disable All
Save Interfaces
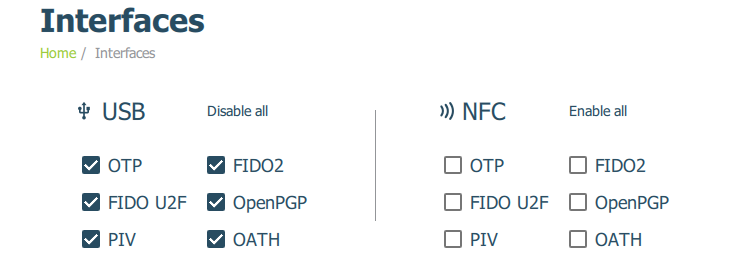
All NFC options are disabled to requirement phyiscal presence.
Setup openpgp on Yubikey
Prepare Yubikey to load GPG key material.
$ gpg --card-edit
Reader ...........: Yubico YubiKey OTP FIDO CCID 0
Application ID ...: XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
Version ..........: 3.4
Manufacturer .....: Yubico
Serial number ....: XXXXXXXXXX
Name of cardholder: [not set]
Language prefs ...: [not set]
Sex ..............: unspecified
URL of public key : [not set]
Login data .......: [not set]
Signature PIN ....: forced
Key attributes ...: rsa4096 rsa4096 rsa4096
Max. PIN lengths .: 127 127 127
PIN retry counter : 3 3 3
Signature counter : 0
gpg/card> admin
Admin commands are allowed
gpg/card> passwd
gpg: OpenPGP card no. XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX detected
1 - change PIN
2 - unblock PIN
3 - change Admin PIN
4 - set the Reset Code
Q - quit
Your selection? 3
PIN changed.
Your selection? Q
gpg/card> admin
Admin commands are allowed
gpg/card> passwd
gpg: OpenPGP card no. XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX detected
1 - change PIN
2 - unblock PIN
3 - change Admin PIN
4 - set the Reset Code
Q - quit
Your selection? 1
PIN changed.
Your selection? Q
gpg/card> name
Cardholders surname: {USER LAST NAME}
Cardholders given name: {USER FIRST NAME}
gpg/card> lang
Language preferences: en
gpg/card> url
URL to retrieve public key: https://keybase.io/{USER}/pgp_keys.asc
Note
As shown using https://keybase.io as the location, but any publically accessible location with the public key material will work.
gpg/card> login
Login data (account name): {GPG USER EMAIL ADDRESS}
gpg/card> forcesig
gpg/card> {PRESS ENTER}
Reader ...........: Yubico YubiKey OTP FIDO CCID 0
Application ID ...: XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
Version ..........: 3.4
Manufacturer .....: Yubico
Serial number ....: XXXXXXXXXX
Name of cardholder: {USER FIRST NAME} {USER LAST NAME}
Language prefs ...: en
Sex ..............: unspecified
URL of public key : https://keybase.io/{USER}/pgp_keys.asc
Login data .......: {GPG USER EMAIL ADDRESS}
Signature PIN ....: forced
Key attributes ...: rsa4096 rsa4096 rsa4096
Max. PIN lengths .: 127 127 127
PIN retry counter : 3 3 3
Signature counter : 0
gpg/card> quit
ykman openpgp set-touch aut fixed
ykman openpgp set-touch sig fixed
ykman openpgp set-touch enc fixed
Note
Fixed is the same as on but requires a new certificate to be loaded if this option is ever disabled.