Edge OS
Setup notes for Ubiquiti Edge OS.
Danger
The most recent firmware update (~2019-10) has added telemetry to ubiquity devices; disabled by default.
Block or blackhole trace.svc.ui.com.
Disable UBNT Discovery Service
The UBNT Discovery Service enables other UBNT devices the ability to discover this device.
Danger
This is exposed externally and exploitable. Disable this service.
configure
set service ubnt-discover disable
set service ubnt-discover-server disable
commit
save
Create DHCP Static Entries
Add static DHCP mapping via CLI.
This will map computer to 10.0.0.2 on Test DHCP server using the
MAC address AA:BB:CC:11:22:33.
Changes are reflected in the GUI.
configure
set service dhcp-server shared-network-name Test subnet 10.0.0.0/24 static-mapping computer ip-address 10.0.0.2
set service dhcp-server shared-network-name Test subnet 10.0.0.0/24 static-mapping computer mac-address AA:BB:CC:11:22:33
commit
save
Create DNS / Host Entries
CNAME for IP lookups without DNS; static /etc/hosts mapping.
Simulates NAT Reflection by statically adding multiple hostnames to the hosts file. Works with subdomains as well. This will provide an internal or custom IP for a given DNS request.
Important
Modifications should only be done via the GUI or CLI; do not modify
/etc/hosts manually as these are not recognized/kept by the system across
upgrades and restores.
Add static host mapping via CLI.
This will map computer and computer.example.com to 10.0.0.2.
Changes are reflected in the GUI. It will appear in /etc/hosts as:
10.0.0.2 computer.example.com computer
configure
set system static-host-mapping host-name computer.example.com inet 10.0.0.2
set system static-host-mapping host-name computer.exmaple.com alias computer
commit
save
Add static host mapping via GUI.
Ubiquiti
Note
preview and Apply. When doing the initial leaf creation, you will get a failure message because it is not configured with an alias or network address yet. This is normal.
config tree › system › static-host-mapping › host-name › Add
host-name
FQDN
Updated: None
Ubiquiti
Note
preview and Apply. Aliases should all resolve to the same IP (base host). Verify by resolving both names on your network.
Important
With later versions of debian based systems, entries in the local host
file for the system will resolve to 127.0.1.1. This is by design.
The alias will resolve to network IP.
The hostname will resolve to
127.0.1.1.
config tree › system › static-host-mapping › host-name › FQDN
alias
FQDN
alias
ALIAS
inet
IP
Updated: None
Add static host mapping via /etc/hosts.
Danger
Provided only in case of need. Do not use this method as changes are not tracked by sysem across upgrades and restores.
/etc/hosts EdgeOS CLI.12.12.12.12 computer.example.com computer # resolve to 12.12.12.12
12.12.12.12 computer2.example.com computer2 # resolve to 12.12.12.12
/etc/init.d/dnsmasq force-reload
Hairpin NAT (Internal Only NAT Reflection)
Generally split-DNS is better to use than Hairpin NAT as it allows more control. This will enable you to redirect internal requests destined for your external IP to another internal destination based on selected criteria. You will need to do this for every subnet on the network.
This may be used for faking subdomains, assuming there is a wildcard DNS setup on your Registrar and it resolves to your public IP.
Hairpin NAT (Internal Only NAT Reflection)
Note
Do not use WAN interface for the Inbound Interface. Defaults for everything else.
Firewall/NAT › Port Forwarding
WAN Interface
eth3
Hairpin NAT
☑ Enable hairpin NAT (also known as ‘NAT loopback’ orn’NAT reflection’)
LAN Interface
eth0.5
Updated: None
Deleted DHCP Host Still Resolves in DNS
When deleting a DHCP host, the DNS reservation should be removed as well. However there is a bug in which these hosts are never deleted.
/etc/hosts EdgeOS CLI.#Delete hosts which are no longer used and reboot the router.
DNS Hostnames not Resolving
DHCP server on the edgerouter needs to update the hosts file when new IP’s are issued.
Enable Dynamic DNS
config tree › service › dhcp-server › dynamic-dns-update
Enable
true
Updated: None
Allow Subnet (Wifi) Traffic Internet Only Access
May be applied to any subnet that should only have Internet access.
Create network group that contains all private IPv4 addresses.
Define RFC1918 Private Address Group
Firewall/NAT › Firewall/NAT Groups › Add Group
Name
RFC1918
Description
Private IPv4 address space
Group Type
☑ Network Group
Updated: None
Define Networks within RFC 1918
Note
Use add new to add each individual network. Be sure to save.
Firewall/NAT › Firewall/NAT Groups › RFC1918 › Actions › Config
Network
192.168.0.0/16
Network
172.16.0.0/12
Network
10.0.0.0/8
Updated: None
Prevent Wifi Traffic from Reaching Internal Networks
WIFI_IN Creation
Firewall/NAT › Firewall Policies › Add Ruleset
Name
WIFI_IN
Description
Wifi to LAN
Default action
☑ Accept
Default Log
☐
Updated: None
Drop Wifi to LAN Basic
Firewall/NAT › Firewall Policies › WIFI_IN › Actions › Edit Ruleset › Add New Rule › Basic
Description
Drop Wifi to LAN
Action
☑ Drop
Protocol
☑ All protocols
Updated: None
Drop Wifi to LAN Destination
Note
This can be done in the previous step by switching tabs.
Firewall/NAT › Firewall Policies › WIFI_IN › Actions › Edit Ruleset › Drop Wifi to LAN › Actions › Destination
Network Group
Private IPv4 address space
Updated: None
Drop Wifi to LAN Interface
Warning
Ensure Interface is set to the appropriate Wifi interface or VLAN.
Firewall/NAT › Firewall Policies › WIFI_IN › Actions › Interfaces
Interface
WIFI
Direction
IN
Updated: None
Only Allow DNS Traffic to Router
Only Allow DNS Traffic to Router
Firewall/NAT › Firewall Policies › Add Ruleset
Name
WIFI_LOCAL
Description
Wifi to Router
Default action
☑ Drop
Default Log
☐
Updated: None
Drop Wifi to LAN Basic
Firewall/NAT › Firewall Policies › WIFI_LOCAL › Actions › Edit Ruleset › Add New Rule › Basic
Description
Allow DNS
Action
☑ Accept
Protocol
☑ Both TCP and UDP
Updated: None
Drop Wifi to LAN Destination
Note
This can be done in the previous step by switching tabs.
Firewall/NAT › Firewall Policies › WIFI_LOCAL › Actions › Edit Ruleset › Drop Wifi to LAN › Actions › Destination
Destination
53
Updated: None
Drop Wifi to LAN Interface
Warning
Ensure Interface is set to the appropriate Wifi interface or VLAN.
Firewall/NAT › Firewall Policies › WIFI_LOCAL › Actions › Interfaces
Interface
WIFI
Direction
LOCAL
Updated: None
DNAT for Captive DNS
Force all DNS queries regardless of destination server to a specific DNS server.
Danger
Do not enable this for the custom DNS server!
Add a Destination NAT Rule for each interface serving internal networks:
Captive DNS Destination Setup
Note
Note the ! to negate matching for destination address. IP is the DNS server.
Firewall/NAT › NAT › Add Destination NAT Rule
Description
NETWORK Captive DNS
Enable
☑
Inbound Interface
INTERFACE
Translations Address
IP
Translations Port
53
Exclude from NAT
☐
Enable Logging
☐
Protocol
☑ Both TCP and UDP
Source Address
IP NET / CIDR
Destination Address
!IP
Destination Port
53
Updated: None
Add Masquerade NAT Rule for each interface serving internal networks. This enables appropriate transparent DNS lookups (Clients will think that they are resolving from the DNS they requested, not the actual DNS server serving responses):
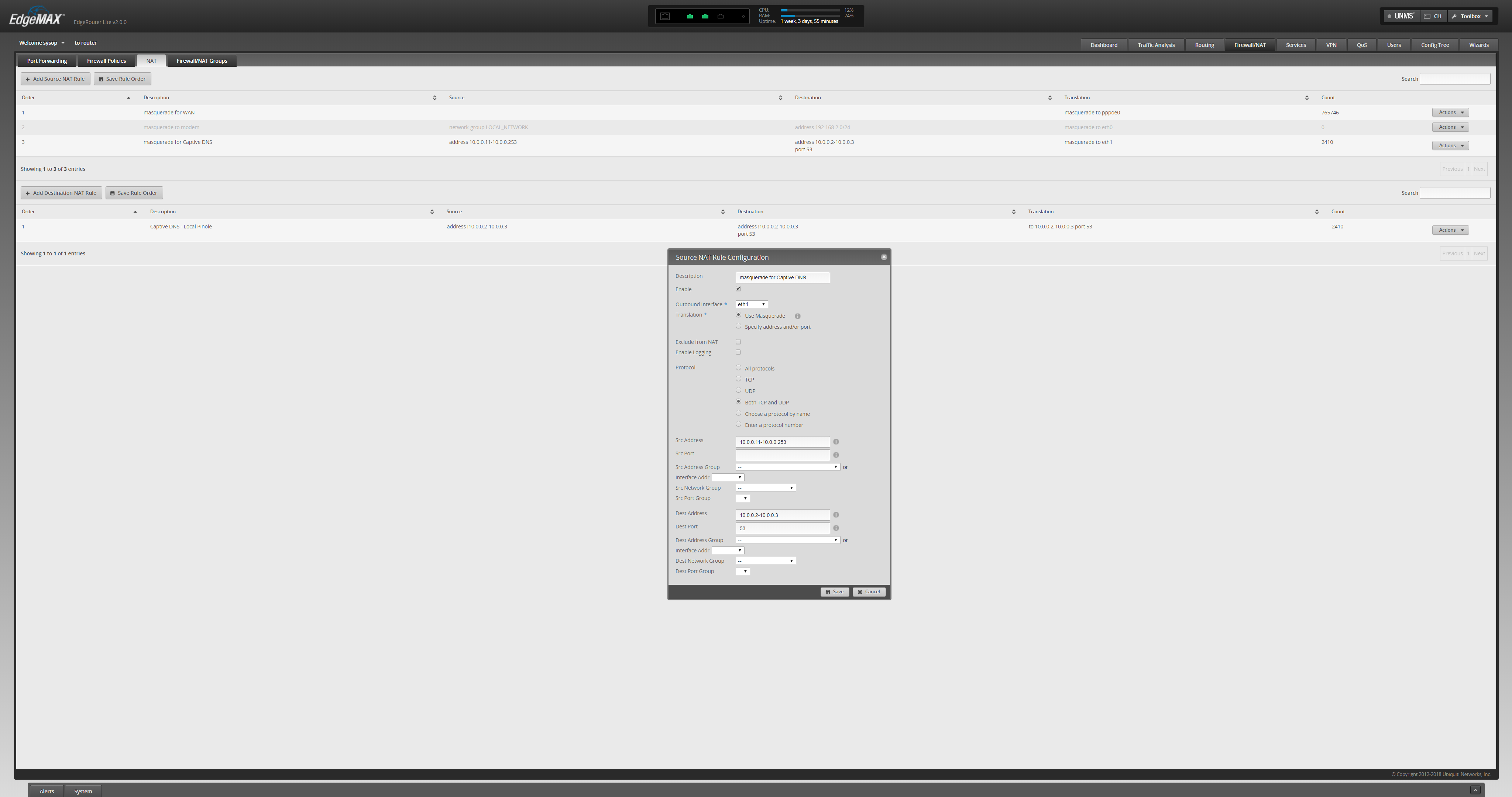
Captive DNS Masquerade Setup
Firewall/NAT › NAT › Add Source NAT Rule
Description
NETWORK Captive DNS
Enable
☑
Outbound Interface
INTERFACE
Translation
☑ Use Masquerade
Exclude from NAT
☐
Enable Logging
☐
Protocol
☑ Both TCP and UDP
Source Address
IP NET / CIDR
Destination Address
IP
Destination Port
53
Updated: None
Captive DNS Exceptions
Allow for specific client exceptions to DNAT rules. These should be an exception and not the rule. Keep this list small.
Create a Source Address Group to manage all clients for the exception:
Create Captive DNS Exceptions Group
Firewall/NAT › Firewall/NAT Groups › Add Group
Name
NETWORK-dnat-exception-group
Description
Disable DNAT / Captive DNS for exceptions
Group Type
☑ Address Group
Updated: None
Add Clients to Exceptions Group
Firewall/NAT › Firewall/NAT Groups › NETWORK-dnat-exception-group › Actions › Edit
Address
IP
Updated: None
Add an additional Destination NAT Rule for each interface serving internal networks:
Captive DNS Destination Exceptions Setup
Warning
Set rule above the captive DNS rule for the specific network for the exception to apply. IP is router.
Firewall/NAT › NAT › Add Destination NAT Rule
Description
NETWORK Captive DNS Exceptions
Enable
☑
Inbound Interface
INTERFACE
Translations Address
IP
Translations Port
53
Exclude from NAT
☐
Enable Logging
☐
Protocol
☑ Both TCP and UDP
Source Address
NETWORK-dnat-exception-group
Destination Port
53
Updated: None
Custom SSL Certifcate for Webface
A custom SSL certifcate may be used to serve HTTPS router traffic. Turn on EdgeOS SSH.
cat privkey.pem cert.pem > server.pem
cp /etc/lighttpd/server.pem /etc/lighttpd/server.pem.Backup
mv /tmp/server.pem /etc/lighttpd/server.pem
kill -SIGINT $(cat /var/run/lighttpd.pid)
/usr/sbin/lighttpd -f /etc/lighttpd/lighttpd.conf
Dump Configuration via CLI Command Export
Export the list of CLI commands to manually re-create the current configuration of the router.
show configuration commands
Dump Configuration to JSON-like file
Show a JSON-like representation of the current router configuration.
show configuration all
References