Manjaro GPG Yubikey
Configure Yubikey for SSH authentication on Manjaro based linux.
Required Materials
Pre-configured Yubikey using Export GPG Subkeys to Yubikey.
sudo pacman -Syu gnupg pcsclite ccid hopenpgp-tools yubikey-personalization
sudo systemctl enable pcscd.service
sudo systemctl start pcscd.service
Configure GPG/GPG Agent
This will enable SSH usage with the gpg-agent.
wget https://raw.githubusercontent.com/drduh/config/master/gpg-agent.conf -P ~/.gnupg
~/.gnupg/gpg-agent.conf# https://github.com/drduh/config/blob/master/gpg-agent.conf
# https://www.gnupg.org/documentation/manuals/gnupg/Agent-Options.html
enable-ssh-support
ttyname $GPG_TTY
default-cache-ttl 60
max-cache-ttl 120
pinentry-program /usr/bin/pinentry-curses
#pinentry-program /usr/bin/pinentry-tty
#pinentry-program /usr/bin/pinentry-gtk-2
#pinentry-program /usr/bin/pinentry-x11
#pinentry-program /usr/bin/pinentry-gnome3
#pinentry-program /usr/local/bin/pinentry-curses
#pinentry-program /usr/local/bin/pinentry-mac
Download gpg-agent.conf
~/.gnupg/gpg.conf# https://github.com/drduh/config/blob/master/gpg.conf
# https://www.gnupg.org/documentation/manuals/gnupg/GPG-Configuration-Options.html
# https://www.gnupg.org/documentation/manuals/gnupg/GPG-Esoteric-Options.html
# Use AES256, 192, or 128 as cipher
personal-cipher-preferences AES256 AES192 AES
# Use SHA512, 384, or 256 as digest
personal-digest-preferences SHA512 SHA384 SHA256
# Use ZLIB, BZIP2, ZIP, or no compression
personal-compress-preferences ZLIB BZIP2 ZIP Uncompressed
# Default preferences for new keys
default-preference-list SHA512 SHA384 SHA256 AES256 AES192 AES ZLIB BZIP2 ZIP Uncompressed
# SHA512 as digest to sign keys
cert-digest-algo SHA512
# SHA512 as digest for symmetric ops
s2k-digest-algo SHA512
# AES256 as cipher for symmetric ops
s2k-cipher-algo AES256
# UTF-8 support for compatibility
charset utf-8
# Show Unix timestamps
fixed-list-mode
# No comments in signature
no-comments
# No version in output
no-emit-version
# Disable banner
no-greeting
# Long hexidecimal key format
keyid-format 0xlong
# Display UID validity
list-options show-uid-validity
verify-options show-uid-validity
# Display all keys and their fingerprints
with-fingerprint
# Display key origins and updates
#with-key-origin
# Cross-certify subkeys are present and valid
require-cross-certification
# Disable caching of passphrase for symmetrical ops
no-symkey-cache
# Enable smartcard
use-agent
# Disable recipient key ID in messages
throw-keyids
# Default/trusted key ID to use (helpful with throw-keyids)
#default-key 0xFF3E7D88647EBCDB
#trusted-key 0xFF3E7D88647EBCDB
# Group recipient keys (preferred ID last)
#group keygroup = 0xFF00000000000001 0xFF00000000000002 0xFF3E7D88647EBCDB
# Keyserver URL
#keyserver hkps://keys.openpgp.org
#keyserver hkps://keyserver.ubuntu.com:443
#keyserver hkps://hkps.pool.sks-keyservers.net
#keyserver hkps://pgp.ocf.berkeley.edu
# Proxy to use for keyservers
#keyserver-options http-proxy=http://127.0.0.1:8118
#keyserver-options http-proxy=socks5-hostname://127.0.0.1:9050
# Verbose output
#verbose
# Show expired subkeys
#list-options show-unusable-subkeys
Download gpg.conf
See Import GPG Master Public Key for importing your public key and assigning ultimate trust for use.
~/.bashrcexport GPG_TTY="$(tty)"
export SSH_AUTH_SOCK=$(gpgconf --list-dirs agent-ssh-socket)
gpgconf --launch gpg-agent
gpg-connect-agent updatestartuptty /bye > /dev/null
Verify SSH Works
Ensure Yubikey is readable by GPG. This assumes you already setup:
~/.ssh/authorized_keyson the target machine with your exported GPG SSH RSA Public Key; see Export GPG Keys. Reference SSH for remote SSH configuration.Trusted the GPG Master Public Key on the local machine; see Import GPG Master Public Key.
Connect with SSH as normal.
A
Pin Entrypop-up window should appear. It may not be in focus. Enter your user PIN.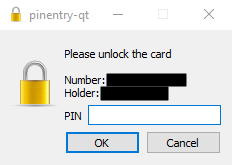
OK
There will be no prompt in putty, but the Yubikey will start blinking. Tap Your Key to login.
Note
Number is the Yubikey serial number.
Holder is the First/Last name of the GPG certificate on the key.
Your key will blink when waiting for password or touch.